Most people don’t know what security headers are. That’s a shame because implementing no or very lax content security policies puts you and your online content at tremendeous and unnecessary risk.
Tightening your web server security takes very little effort if you know what you’re doing. Instead of rewriting what others have said better, let’s just link to a brilliant write-up on HTTP Security Headers Best Practices. (Also, we like short posts. 1000+ word bloated “articles” are for Indian wannabe-SEO-gurus.)
We have mentioned SecurityHeaders.io before, but we see no reason not do it to again.
OK, so most people have this vague feeling that “SSL certificates are good”. So they buy one, install it and think they’re all set. Things are unfortunately not that simple.
We find it surprising that so many big players hit and miss. We mean, REALLY big players. Washington Post has approximately one billion page views per month, according to themselves.
Let’s look them up. Here’s the sad result as of today.
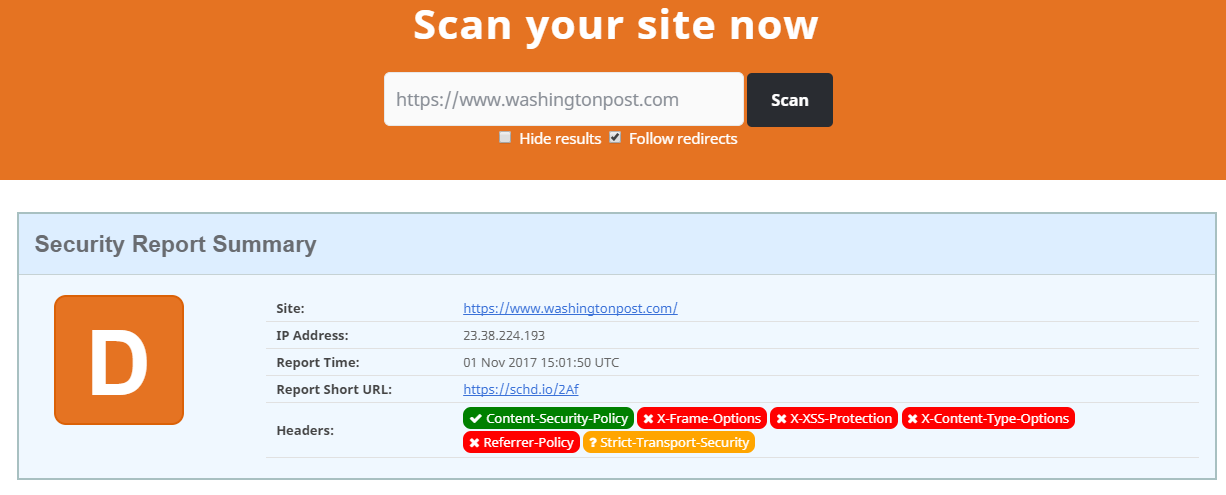
D – Are you kidding us? (Here’s a link to the results; sure hope it looks better when you look them up.)
With one billion page views, they should be able to afford someone to fix this for them. It shouldn’t take more than a couple of hours. One could alternatively think of it this way – how can they afford not to? It takes one damn line of code to shut the door for a simple XSS attack. Come on!
Speaking of money… Why do people and businesses buy SSL certificates in the first place, when they are free? Let’s Encrypt, for example, issue SSL certificates at no cost at all, and provide excellent guides on how to get, set up and use them. And yes, they work just fine on shared hosting, contrary to whatever your web hotel is trying to sell you.
So, how are our own HTTP security headers holding up? Like so. That’s how we roll.
A+, baby.
hey how are you today man?
I’m just fine hacking your wp site